Right after food, water, and air, I (personally) think the internet is one of the best things to happen to man. There are about 7.7 billion people on earth and according to WeAreSocial.com, over 4 billion people use the internet in 2019. That’s more than half of the world’s population.
The internet is a beautiful place; a medium to obtain & exchange information, work, have fun, make money, communicate, meet people, learn stuff, and do a whole lot more. However, despite the good that the internet has to offer, things can get really ugly as well.
In so many different ways, people have been scammed on the internet, their monies (and identities) have been stolen, accounts have been compromised and so on. And these things are avoidable. Carefully go through this guide to have a full understanding of how you can stay protected on the internet — on mobile & mobile apps, PC & desktop software, etc.
A. General Security and Authentication
i. Protect yourself from other individuals
Before now, a good number of internet users accessed the web via laptops and desktops. Things are quite different now as smartphones and mobile apps have disrupted PC. And since, unlike PC, smartphones can get stolen or misplaced easily, the very first step of securing your online accounts is creating strong passwords, PINs, and patterns. Biometric authentication methods like fingerprint, Face ID, Iris scanning, and Palm Unlock are also other secure ways of protecting your smartphone and mobile app.
There are times when you aren’t sure if your account passwords have been compromised or not. There are certain tools (like Google Chrome’s Password Leak Detection ) that help you figure out which of your passwords have been compromised in data breaches.
The list below contains links to useful information, tutorials, and guides that’ll help you strengthen your mobile and app security. And ultimately, protect you from any harm on the internet.
Useful Links:
- Complete Guide to Smartphone Biometric Authentication: (Fingerprint, Iris, Voice, Face ID)
- Why you shouldn’t use Fingerprint/Touch ID and Face ID
- How to enable Password Leak Detection in Chrome
- Google Chrome’s new extension checks if your Password has been breached
- How to change or reset forgotten Google password
- How to change or reset forgotten Facebook password
- How to password protect your Android Apps
- How to recover a hacked Facebook account
ii. Creating Strong Passwords
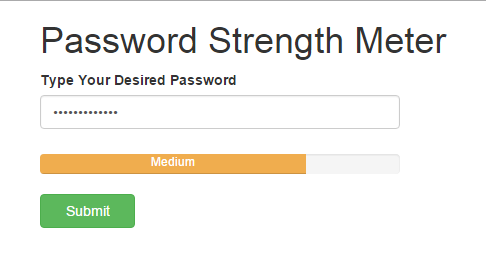
Anything worth doing is worth doing well, they say. The same applies to creating passwords to safeguard your accounts on the internet. You shouldn’t just create passwords for the sake of it. Your password should be “strong”. It should contain a balanced mix of certain elements and ultimately, be very difficult to hack, guessed, or bypass. And yes, there are some passwords you should NEVER use to secure your accounts. Check them out .
If you’re having a hard time creating a strong password, you should check out our detailed guide on creating strong passwords . Alternatively, you can use password managers — software/apps that suggest strong passwords for your online accounts and also helps manage all your passwords so you don’t have to always remember them.
Useful Links
- What makes a password “strong”?
- How to use the Google Password Checkup extension to keep your accounts secure
- These are the Top 25 Worst passwords of 2018
- How to Use a Firefox Master Password to Protect Stored Logins and Passwords
iii. Two-Factor Authentication — Passwords aren’t enough
Sometimes, it’s not even enough having a strong password; you should further beef up your mobile account’s security via 2-Factor Authentication (also called 2FA or 2-Step Verification ). Enabling 2FA in your online accounts will require you input some sort of code (in addition to your password) which would be sent to your phone number as a text, to a physical token, or the authenticator app on your smartphone.
We have put together a comprehensive guide on everything you need to know about 2-Factor Authentication — when, why and how to use it to secure your account online.
Other Useful Links
- Lock down your Google and Facebook account with Two-Factor Authentication (2FA)
- Correctly Configure Two-Factor Authentication before you’re locked out of your own account
- How to sign in to a 2FA-enabled Google account when you lose your phone
- How to Increase your Online Security by Enabling Two-Step Verification
B. Online & Web Privacy
Because the internet is filled with hackers, spammers, sniffers and prying eyes with evil intents waiting to steal your data at every chance they get. This is why it is important to keep yourself (and your information) protected at all times.
i. VPN & Proxies

As earlier mentioned, the internet is one place where you want your privacy respected on all fronts. However, this is something you need to pay keen attention to because the hackers are also not sleeping. One way to keep your online privacy strong is by concealing your internet traffic. And you can achieve that using VPN and Proxies.
Asides from bypassing geo-restrictions, VPNs and Proxies are also brilliant ways to conceal your identity from evil eyes on the internet.
Useful Links
- What Exactly is a VPN (Virtual Private Network) and Why You Still Need One
- The difference between a Proxy and a VPN
- How to Keep Your Internet Traffic Private from Anyone
- Here’s how to choose between Free and Paid VPN
- How to selectively use VPN for specific Apps only on your phone
- Cloudflare’s WARP is a Free fast VPN with no Ads. Here’s how to get it
ii. DNS-over-HTTPS
Hackers, spoofers, and individuals aren’t the only ones that constantly lurk on the internet to steal your data. Corporations do it too. Sometimes, your internet service provider (ISP) harvests personal data about your activities on the web and sells to third-parties —who in turn use such info for advertising targeting— without your consent. Not all ISPs do this but the truth is, there’s really no way for you to find out if they do… or not.
What you can do, however, is to use privacy-focused technologies like DNS-over-HTTPs to protect your personal privacy on the web. You can further read about such technologies and how to use them to safeguard yourself and your data on the web.
Useful Links
- What’s DNS-over-HTTPS (DoH) and DNS-over-TLS (DoT) and why it’s controversial
- How to Enable DNS-over-HTTPS(DoH) in Firefox and Chrome browsers
- How to change DNS server on Windows, Mac and Linux
- How to change the DNS Server on your Phone
iii. HTTPS & SSL certificates
When you surf the web in your browser, some websites URL start with http:// and some, https://. The additional “S” has a meaning to it and you should ensure that whatever website you’re surfing on the world wide web has a https:// at the beginning of the URL.

The extra S stands for Secure Sockets Layer (SSL) and is an indication that your connection with the website is private and whatever information you provide on the site cannot be intercepted by a third-party who may want to use it for fraudulent activities. Whenever you’re surfing a website that doesn’t have the SSL certificate, some browsers (especially Chrome) will alert you that the website isn’t secure. Whenever you this warning, make sure you do not provide sensitive information on the website.
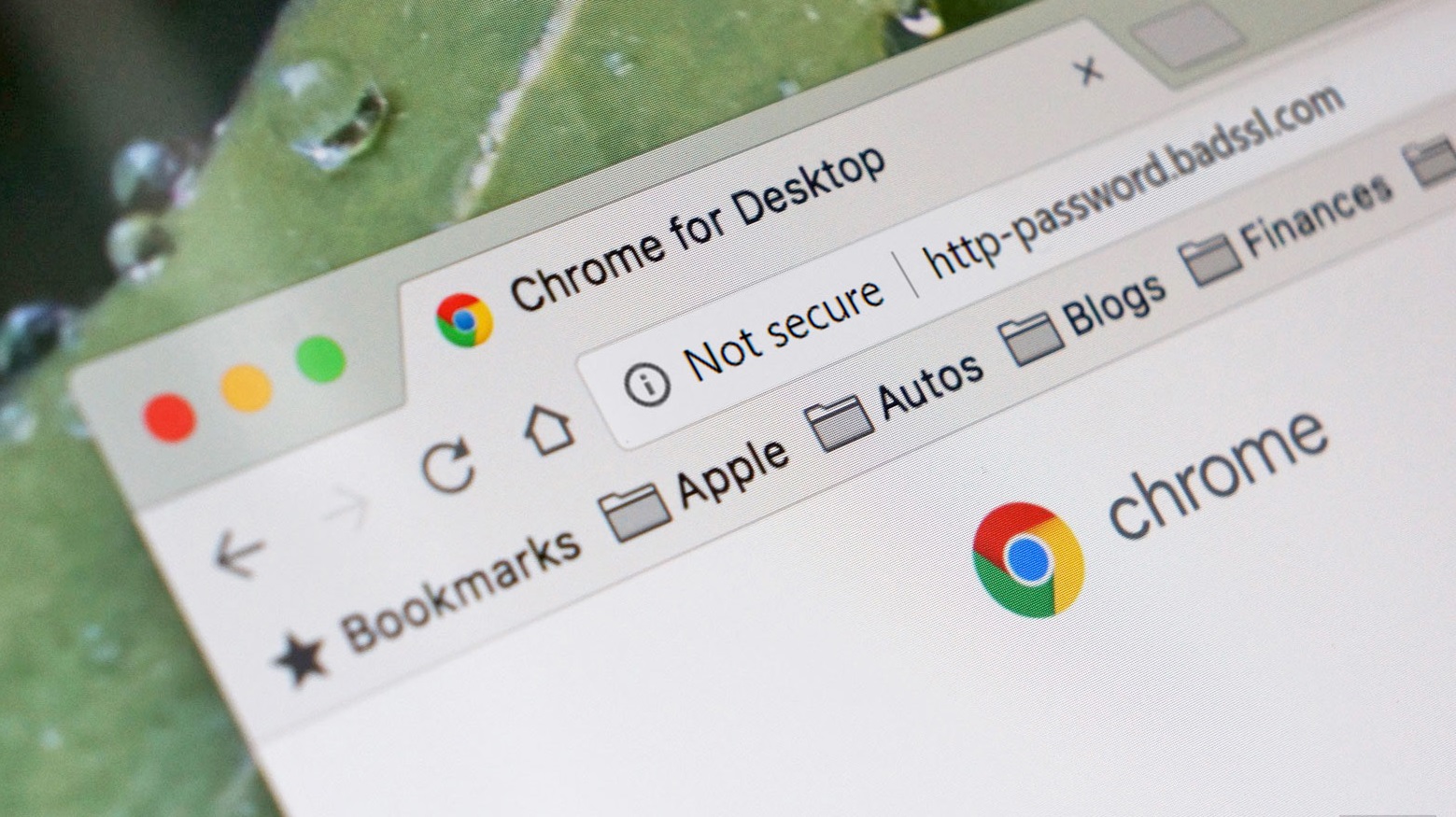
SSL (Secure Sockets Layer) is the standard technology for keeping an internet connection secure and safeguarding any sensitive data that is being sent between two systems (like a website and a server) so as to prevent criminals from reading and modifying any information transferred, including potential personal details, credit card details, bank login credentials, passwords, etc. Advertisement - Continue reading below
Useful Links
- What are SSL certificates? Understanding how useful they are
- Why do website addresses start with http:// or https://
- Should be worried about “not secure” chrome warning on non-https websites?
- For website owners — A complete guide to running your website securely on https
iv. Privacy-focused Browsers & Search Engines
Not sure if you know this but the moment you log onto the internet, you leave a trace that tells a lot about you to certain people and corporations. Your browser, for example, knows more than you think. Asides the fact that it (your browser) takes note of your browsing history, other data like location information, operating system details, plugins installed, time zone the computer is set to, language, screen size and other information are garnered through a process known as “fingerprinting”.
Some browsers are also not generally secure and allow hackers and third-parties access your data so easily. That’s why should consider using privacy-focused browsers . These privacy-focused web browsers limit ads, incessant spam, monitoring, and tracking to the barest minimum.
About search engines, they also collect and harvest a lot of your personal information. That’s the (hidden) price you pay for using their services for free. The solution to keeping your private information private when searching for information online is to use privacy-focused search engines — DuckDuckGo is a good example.
Useful Links
- Getting started with DuckDuckGo, the privacy-focused search engine
- Top 5 Privacy-focused Browsers To Have on Your Desktop
- Here’s what your Browser knows about you
v. Disposable Email Providers
Another service that you can use to beef up your online privacy & security is Disposable emails. Also known as “Throw-away email”, “Tempmail”, “Fake-mail”, or “Trash mail”, Disposal email providers offer these service that allows you receive emails at a temporary address that self-destructs after a certain time elapses. No sign-up or password is required.
Useful Links
- Top 3 disposable email addresses service providers
vi. Phishing and Scams
For noobs and newbies, phishing is when hackers or evil perpetrators maliciously keep (and operate) a false website or send a false e-mail with the intent of masquerading as a trustworthy entity with the intent of acquiring sensitive information such as usernames, passwords, login credentials, credit card details, etc.
Useful Links
- How to avoid Phishing Online
- 5 ways to protect yourself from Ransomware
C. Mobile Security
Because the majority of the online activities (shopping, social media, gaming, surfing, movies, streaming, etc) happen on our smartphones and tablets through mobile apps, it is important to learn how to keep your privacy intact while using them.
i. App permissions
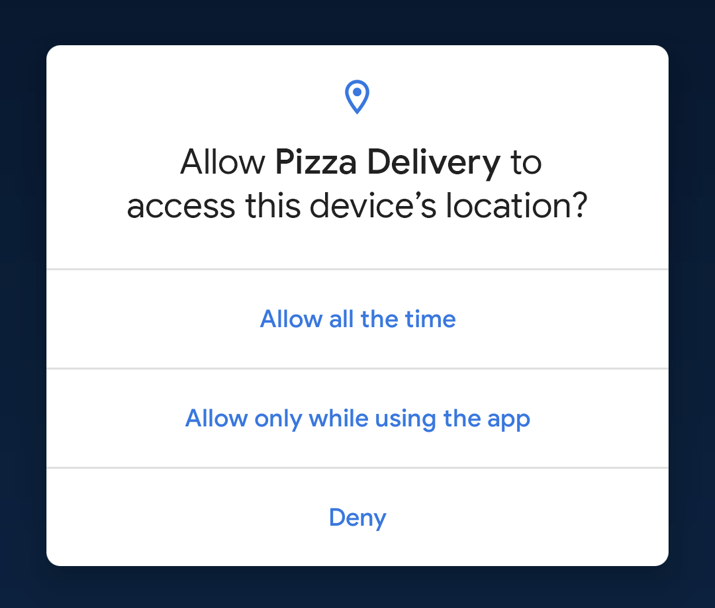
When you newly install an app, it mostly requires you to approve certain permissions. These permissions usually give these apps access to personal & private information like your location, files, microphone & mic recordings, and other data that can be used to track you.
The links below will navigate you through things you need to do to keep your private info from the reach of certain apps.
Useful Links
- Android Permissions: What do apps have access to on your device?
- App permissions you should keep an eye on
- What to consider before installing an app on your phone
- How Geo-tagged photos give away your location
- How to Prevent Facebook from Background Location Tracking on Android
ii.Pop-up Ads
Pop-ups and malware are another thing you should keep an eye out for. These are malicious apps designed to steal your information and also cause damage to your device. Pop-ups drain your phone’s battery, increase your device temperature, and generally make your device run slower. Worst part is that they are “stubborn” i.e. sometimes very difficult to uninstall or remove fro your device.
- How to Stop and Remove Pop-up Ads on Android devices
- If you have any of these 85 apps on your Android smartphone, UNINSTALL them now
iii. Geo-tagging
Despite the fact that the average internet user is now more privacy-conscious about the type of information shared online, we still subconsciously give out certain (sensitive) data without even realizing it.

Geo-tagging is the process of attaching location information to media files like photos and videos. When a media file is “geo-tagged”, it basically means that the device (digital camera, smartphone, tablet, etc.) that captured the file has embedded GPS coordinates in the file metadata.
Although geo-tagging a photo has some useful applications like helping you organize pictures in your gallery based on location, it also comes with its associated (privacy) risks too. A stranger can download your pictures on the internet, extract GPS coordinates and track you.
Useful Links
- How Geo-tagged photos give away your location
- Should you always have your phone’s GPS Location turned on?
D. Banking, Payments & Mobile Money

The rise of eCommerce, cryptocurrency, mobile money, fintech apps, payment apps, virtual cards and the like have subsequently increased how much people transact over the internet. In Africa and across the globe. Equally, the number of time people have been scammed while transacting online and their assets stolen have likewise increased.
Since the majority of transactions carried out online are performed using credit and debit card, it is important to know the anatomy of your banking (debit and credit) cards, measures you can take to avoid being defrauded, as well as what you should do if your card/logins are stolen.
As an added layer of security when transacting online, ensure that extra authentication steps like 2-Factor Authentication and One-Time Password/PIN (OTP) are enabled on your banking and payment apps.
The articles linked below contain everything you need to know about staying safe while transacting online.
Useful Links
- Debit and Credit card number, CVV and Expiry date explained
- Debit card vs. Credit card: What are the differences?
- How to avoid credit/debit card fraud
- What you can do when your Debit/ATM card is stolen
- What is one-time password or one-time PIN (OTP)?
- How to change your Mobile Money PIN. (MTN, Airtel and Africell)
- What happens if someone steals your mobile money PIN?
- How to change your Safaricom M-PESA PIN
E. Email Protection

Email is one of the most used media of communication, both for personal and business purposes. There are about 4 billion email users worldwide and over 293 billion emails are sent each day (according to 99firms.com ).
As such, email (and email accounts) are mostly targetted by hackers and spammers. There are a lot of security methods listed above that helps protect your emails but we’d be linking more email security resources and tips below.
Emails are secure, but not always. If you had previously granted any third-party apps, software or developers access into your inbox, they can read your emails. So you should review the permissions you might have given to third-party apps in the past. You might also want to confirm that your email provider offers end-to-end encryption.
Useful Links
- 5 email providers that offer end-to-end encryption
- How to Block third-parties from accessing your Gmail
- How to reset your Yahoo password
F. Social Media

Everyone uses social media but not everyone is using it safely. By safely, we mean what are the things your social media platforms know about you? Do they collect more data than you permit them to? What type of information does your social media platforms collect from your (and behind your back)? Are your social media accounts well-protected from hackers? So many questions.
Luckily, there are answers to all of them. In this era where many social media platforms have been caught harvesting and selling their user data to the highest bidder, using social media safely and being conscious of what data they obtain from you is quite important.
The links provided below might help you.
Useful Links
- 10 ways you can improve security of your Facebook account
- How to delete auto-uploaded phone contacts on Messenger
- Social Media, Election fever and how to protect yourself online from your government
- How to view & download all your WhatsApp account information
- How to download your Twitter account information
- How to delete your phone contacts uploaded on Facebook
- How to delete your Facebook Account Permanently
- How to recover a hacked Facebook account
Wrap up
Just as technology keeps evolving, privacy (and security at large) as an aspect of the internet will also keep on evolving. Currently, the links and materials listed above will solve a good number of privacy and security challenges that you (as a user/consumer) currently face. As more privacy-focused technologies and solutions are developed, we’ll add them to this list as soon as possible. So ensure you bookmark this page on your browser if you really do care about privacy.
Sodiq Olamide is a tech writer based in Nigeria, covering the latest reviews, how-tos, and news on consumer tech trends with a unique African perspective. Whether analyzing emerging technologies or offering practical guides, Sodiq brings a deep understanding of how technology shapes lives across the continent.
Type your email…
Talkio Mobile , Uganda’s newest telecommunications service provider, is excited to announce a groundbreaking partnership with Banana Life Investments, a leading chain of mobile phone and retail shops. This strategic alliance aims to bring Talkio’s innovative telecom services closer to Ugandans.
This collaboration will leverage Banana Life Investments’ extensive retail network of 26 stores strategically located across Uganda in major malls, towns, and cities to provide customers with unparalleled convenience. Through this partnership, Talkio Mobile will offer its full suite of services, including SIM cards, airtime, and exclusive product offerings at any Banana Life Investment location.
This partnership is more than a business initiative—it’s a shared commitment to transforming lives. By integrating Talkio Mobile’s forward-thinking services & nationwide reach with Banana Life Investments’ retail footprint, the two brands are setting a new standard for customer convenience and inclusivity.
READ ALSO: 5 Things You Need to Know About Talkio Mobile: New Telecom Company in Uganda
“This partnership aligns perfectly with our mission of connecting Ugandans to innovative and transformative telecom solutions,” said Vianne Allan Ahura, CEO of Talkio Mobile. “By leveraging Banana Life Investments’ trusted presence and nationwide footprint, we are not only expanding our agent network but also bringing our services closer to the communities we serve. This collaboration ensures that our online customers can now enjoy a seamless offline experience right at their doorstep. Together, we are empowering Ugandans with the tools they need to stay connected, grow their businesses, and unlock new opportunities.”
Solomon Ssemuyaba, the assistant general manager at Banana Life Investments, echoed this sentiment: “We are proud to join hands with Talkio Mobile to deliver innovative, customer-centric solutions. This partnership represents our shared vision of fostering a connected future for Uganda. Together, we are redefining what convenience and accessibility mean for our customers.”
The partnership goes beyond retail distribution, introducing joint initiatives aimed at value addition and personalized service. Customers can expect seamless access to:
- SIM Card Sales : Available at all Banana Life Investments locations.
- Talkio phone number bookings : Book your preferred Talkio number at any Banana Life Investments location.
- Airtime Services : Recharge easily through in-store purchases.
- Customer Support : Friendly and knowledgeable staff trained to assist with Talkio Mobile products and services.
Additionally, the two companies plan to launch promotional campaigns and expand services to even more locations, ensuring no Ugandan is left behind in the digital transformation.
Solomon Obwot is a tech writer based in Kampala, Uganda, with extensive experience in the local tech startup ecosystem. He covers the latest news and analysis on consumer tech, writes in-depth smartphone reviews, and conducts insightful interviews with industry experts. Solomon is also a passionate podcaster, sharing his knowledge and engaging in discussions about Africa’s rapidly growing tech landscape. Send emails to [email protected]
Type your email…
Smartphones have, over the years, become a very important aspect of our lives. Its use has transgressed from basic communication (calling, texting, etc.) to our everyday work and personal lives. Nowadays, the average smartphone user stores personal files, multimedia, and other documents — banking details, social media, internet banking applications, shopping, work and personal emails etc. — on his device that could cost a fortune if in the wrong hands. This is where smartphone security comes in.
For years, numerical passcodes and alphanumeric passwords were how we kept trying eyes away from the contents of our devices. Now, smartphone manufacturers have stepped things up a notch by complementing the regular form of smartphone security with biometric authentication. And quite impressive enough, smartphones now sport biometric authentication tools that are were only possible on high-end computers.
We highlight all the biometric authentication technology that have been successfully implemented on mobile phones over the years, their advantages, downsides, prospects they hold, and smartphones that support each authentication methods.
Fingerprint

The fingerprint sensor or reader is one of the earliest biometric authentication technology to feature on a smartphone. The history of fingerprint authentication on smartphones dates back to 2004 when a South Korean company announced the Pantech GI100. The device was the first ever device to have a fingerprint scanner for authentication and speed dialing purposes. However, some sources opine that Apple started the modern-day fingerprint scanner revolution when it launched the TouchID with the iPhone 5s.
Pantech GI100
There are basically three types of fingerprint scanners used on smartphones and they differ in how they function and scan prints.
Optical scanners / sensors
Capacitive sensors
Unlike optical sensors that takes an image of your finger, capacitive sensors make use of capacitor circuits (its core component) to collect fingerprint data. This type of sensor is most used fingerprint sensor.
Ultrasonic sensors
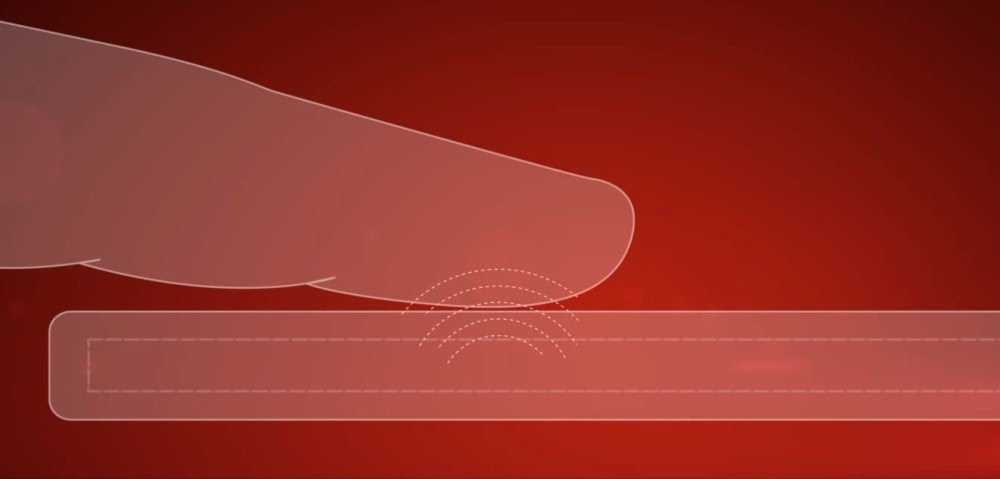
This is a new sensor that was introduced by Qualcomm in 2016 on the LeeCo Le Max Pro. This sensor uses a transmitter to send ultrasonic pulse against your finger to create 3D details of your prints. Only ultrasonic sensors reproduce and store prints in 3D, making the ultrasonic system more secure than 2D versions created by optical and capacitive sensors.
Pros of Fingerprint scanning
Fast unlock time
Can be used for other purposes (like payment authentication) aside device unlock
Cons of Fingerprint scanning
Smartphone can be unlocked without user’s consent i.e when sleeping
Iris Scanner

Iris scanning isn’t a very much popular biometric authentication method on a smartphone, it is also more sophisticated way of securing your smartphone. And though Iris scanning is commonly and mostly used on Samsung Galaxy flagships, the technology was first used on a phone — Fujitsu ARROWS NX F-04G — by Japanese company Fujitsu.
How does Iris Scanning work?
The structure of the human eye.
The Iris is a thin and circular structure in the eye. It adjusts the size of the pupil and also responsible for controlling the amount of light that enters the eye. Interestingly, just like fingerprints, no two humans in the world have exactly the same Iris.
The odds of any two irises being identical has been calculated to be one in 10 raised to the power of 78. Barring injury, the patterns remain stable through life, unlike faces, voices and even fingerprints.
The Iris scanner of your smartphone flashes near-infrared (NIR) light into one or both of your eyes to recognise your iris(es) and unlocks your device. The NIR light emitted by the iris sensor is safe and poses no risk to the user.
“The amount of infrared light is no more than would be received by walking outside on a sunny day.”
Pros of Iris Scanning
- Iris Scanning is more accurate — unlike fingerprint (40), the human Iris has 225 different points of comparison.
- Secures your device while you’re asleep.
Cons of Iris Scanning
- Iris scanners are expensive. Thus making phones with iris scanning capabilities generally pricier.
- Iris scanners can be fooled by a high quality (face or iris) image.
- Iris capture can be delayed if a user isn’t looking properly into the camera or if head isn’t still.
- Scanning under direct sunlight can be a problem since the iris may be obscured by bright reflections.
Some smartphones with Iris Scanning method of biometric authentication include Samsung Galaxy S9 Plus , Samsung Galaxy Note 9, LG G6, HTC U11 etc
Voice Recognition
Also known as Voice ID, Speaker recognition, or Voice Biometrics, Voice recognition is an authentication method that grants access to a device by identifying a user’s unique voice pattern.
How Voice Recognition works (www.howitwork.in)
When identifying and differentiating between voices, a device’s voice recognition software takes the following unique voice biometrics into consideration: sound, rhythm, pattern, dialect, speaking style, pitch, format frequencies and spectral magnitudes.
Pros and Cons of Iris Scanning
Voice recognition is also quicker, easier, and relatively more secure. However, there are reports and fears that a good mimic can bypass voice recognition authentication .
Facial Recognition
Facial recognition on Uhans i8 smartphone
Although Facial Recognition only recently became popular when Apple introduced to the iPhone X as Face ID, the isn’t the first instance the technology would be used on a smartphone. Facial Recognition as a form of smartphone security dates back to 2005 when ORMON Corporation, a global leader in automation, control technology, and sensing announced the OKAO Vision Face Recognition Sensor (which could be used on mobile phones, PDAs, and a y camera-enabled device) in Japan.
How does Facial Recognition works?
Depending on some factors like the manufacturer of your smartphone, facial recognition are of different types, have varying characteristics as well as patterns of functioning. Majorly, many smartphones that comes with the feature usually use the front-facing camera and dedicated software to record an image and properties of your face.
Each time you unlock your smartphone, it uses the front camera for recognition, comparing the original scan to what the camera sees. Advertisement - Continue reading below
Presently, there are many smartphones that comes with Facial recognition capabilities but Apple’s Face ID (on the iPhone X and subsequent iPhones), despite its shortcomings , is one of the most sophisticated.
Face ID on iPhone X
Face ID uses an IR beam projector and Infrared camera to create a 3D model of your face; it measures distance traveled by each beam before they hit your face. It is also the most effective, precise, accurate and safest facial recognition system ever used on a smartphone. Unlike most other facial recognition systems, Face ID takes extrinsic properties of the face like facial hairs, accessories into account. Its effectiveness isn’t hindered by growth or accessories as Face ID software automatically and occasionally recaptures and updates your facial template.
Pros
- Convenience — Facial Recognition might not be the safest method of biometric security, but you don’t have to tap buttons, keys, or touch any part of your smartphone before it unlocks.
- Fast and easy to set up
- Effectiveness not hindered by facial growth and accessories
Cons
- Intruders can gain access to your device if you’re asleep by simply placing your phone to your face.
Generally and conclusively, biometric authentication can not entirely replace PIN, passwords, patterns, code etc in terms of security and reliability, they can only supplement. Some of these biometric security systems are still in their early stages and undergoing research and development. Fingerprint sensors, for example, are now being placed under displays. Facial recognition are also becoming faster. It is becoming pretty much obvious that biometric means of authentication is the future of smartphone security.
Sodiq Olamide is a tech writer based in Nigeria, covering the latest reviews, how-tos, and news on consumer tech trends with a unique African perspective. Whether analyzing emerging technologies or offering practical guides, Sodiq brings a deep understanding of how technology shapes lives across the continent.
Type your email…
Over the years, we’ve seen an increase in the number of biometric methods of authentication and sophistication of smartphone security in general. Of all the biometric technologies, however, fingerprint scanner (or Touch ID) and Facial recognition (popularly known as Face ID) stand out and are currently the most used.
This is because these biometric authentications are sleek, fancy, futuristic, and most importantly, fast. But when compared to traditional forms of security (PINS and passwords), fingerprint readers and Face ID suck. And as such, there are times you don’t want to use them to secure your devices.
If you have these two biometric instruments as your preferred method of guarding the (purest, darkest and costliest) digital assets on your smartphone, then you might want to turn them off under these instances.
Fingerprint/Touch ID: why shouldn’t it be used?
1. Fast, but flawed

Fingerprint reader might be faster than typing some 4-digits (or more) PIN or multiple character password. Smartphone users are regularly looking for convenience and means to get things done on their devices faster, so it’s understandable.
However, do you know that your smartphone can be unlocked by a “Master print”? Just the same way a Master key can unlock numerous doors, a “Master print” can also be used to unlock many devices.
Master prints are fingerprints that have been engineered to match multiple patterns. With a 65% success rate, these master prints are able to unlock your device by capitalizing on the small size of your phone’s fingerprint scanner — which only matches a partial scan (rather than all the ridges) of your finger. This is why fingerprint sensors are fast, and at the same time, flawed.
The Master print loophole in smartphone fingerprint sensors was discovered by researchers from New York University and Michigan State University .
Other ways a hacker can fool your fingerprint scanners can be fooled are;
- By using an image/photo of your fingerprint
- Using fingerprint remnants left on objects like cutleries or on your device.
- Using objects like bubble gum, just like this user did with a Nokia 9 smartphone
2.Compulsion to unlock (by Law)
Depending on the country you are (or live in), you can be forced to unlock your device by law enforcement agencies if you locked it using any form of biometric authentication — fingerprint, Face ID, Iris scanning, Palm Unlock , etc. This is because in some countries, coercing a user to divulge his/her device’s PIN or password is a violation of your rights.
On the other hand, an order from a judge/court to unlock your device using Touch ID, Face ID or any other biometric methods isn’t a violation of the law or the user’s rights.
3. Identicality flaw
Your device can be unlocked by another individual with similar characteristics without even trying too hard. This doesn’t apply to Touch ID though because no two persons in the world share the same fingerprint. With Face ID, however, there have been instances where twins, siblings, and two humans with identical facial properties have been able to unlock the same device.
This doesn’t happen with PINs or passwords. Two or more people might have the same passwords or PIN but there really is no way for you to find out unless you’re being told.
4. Face ID can be overridden by a picture/mask
If a hacker can get your printed photo of you and properly places it in front of your smartphone’s selfie camera, (s)he can bypass your device’s facial recognition system. A Samsung Galaxy S8 facial recognition has been hacked using a printed photo in the past. Some Apple flagship iPhone’s have their Face ID security bypass using a printed 3D mask of the user’s face.
5. Fingerprint is eternal
Fingerprints are one feature we all possess that lives with us till death; there’s no changing it. Unlike PINs and passwords that can be changed anytime, fingerprints cannot. And if an intruder clones your fingerprint, he’ll have access to your device, apps, accounts, etc forever. Changing your phone wouldn’t help either.
This is more reason why you should use strong passwords and PIN that only you can remember and are difficult to crack.
There are many instances where these biometric technologies have failed. In fact, they seem to be more easily bypassed (by hackers, the government, and other individuals) than traditional PIN and passwords.
When it comes to securing your device, the best bet is actually an alphanumeric passphrase.
We’ve established the fact that fingerprint sensors and facial recognition aren’t exactly secure, but that doesn’t mean you shouldn’t use them anymore. Not using them, in fact, is almost impossible in this time/era. The message, however, is that you shouldn’t use them for certain things on your smartphone. Here are some.
Don’t use Face ID/Touch ID on these
1. Banking apps
Unlock your smartphone using Face ID and fingerprint might expose you to zero risks if you have no sensitive information on your device. What you shouldn’t do is use fingerprint or Face ID to login to your banking apps. Use pins or (alphanumeric) passwords to secure your banking apps.
Yes, fingerprint and Face ID are faster but are they worth risking the thousands/millions in your bank account for? If you are a deep sleeper, people can log in to your phone without your knowledge using your finger. They can do the same to your bank app and mess with your monies.
Your accounts are safer with PIN/password even while you’re asleep.
2. Paymentapps
Although payments apps like Apple Pay, PayPal and the supports signing-in using fingerprint and Face ID, you should turn them off or deactivate it. Sign-in to your payment apps and authorize transactions using a PIN or password only.
If you lock some other apps (like WhatsApp and Email app) that contain private and sensitive information on your device with fingerprint or any form of biometric tech, you should turn it off today and use PIN/password instead. Biometric authentications are also safe security measures but compared to manually inputted PIN, they are easier to crack.
Fingerprint and Face ID are, no doubts, quick methods of authentication but you shouldn’t use them for everything. Know when to turn them off and when to use them. If you are a high profile individual (politician, journalist, activist, CEO, etc.) you are better off securing your gadgets with PINs and passwords than these two forms of biometric authentications — Face ID and Touch ID.
Sodiq Olamide is a tech writer based in Nigeria, covering the latest reviews, how-tos, and news on consumer tech trends with a unique African perspective. Whether analyzing emerging technologies or offering practical guides, Sodiq brings a deep understanding of how technology shapes lives across the continent.
Type your email…
The Mobile World Congress (MWC) Barcelona , the world’s largest exhibition for the mobile industry, has just concluded. This annual event gathers leading technology brands to unveil groundbreaking mobile, AI, and digital solutions innovations. At MWC 2025, TECNO showcased a range of AI-driven products, reinforcing its commitment to cutting-edge technology.
The key launches included:
- CAMON 40 Series – AI-powered smartphones with One-Tap FlashSnap and advanced mobile imaging features.
- MEGABOOK S14 – The world’s lightest 14-inch OLED laptop, featuring AI-enhanced multitasking and Snapdragon® X Elite.
- MEGABOOK T14 Air & K15S – Lightweight ultrabooks with AI capabilities and extended battery life.
- TECNO AI Glasses Series – Smart eyewear integrating AI imaging, translation, and AR display.
Jan Stryjak, Associate Director at Counterpoint Research, shared, “In the past year, we have observed significant advancements in the field of AI. AI will continue to drive transformative changes in our daily lives. In this critical period for the economic development of emerging markets, TECNO’s AI technologies are unlocking potential for diverse needs.”
“The application of AI technologies is crucial and urgent in emerging markets. We’re committed to bridging the digital gap between emerging and mature markets,” said TECNO CMO, Laury Bai. “TECNO is taking a practical approach to make AI more accessible, ensuring users in emerging markets can access AI and cutting-edge technologies.”
Laury Bai, TECNO CMO
Driven by its commitment, TECNO has forged a robust partnership with MediaTek, establishing a joint AI laboratory dedicated to accelerating advancements in AI. At the event, James Chen, Vice President of Product and Technology Marketing at MediaTek, emphasized, “The synergistic R&D efforts between TECNO and MediaTek are set to democratize AI technology. Our collaboration powers a seamless, interconnected AI experience, bringing users a future of truly connected intelligence.”
James Chen, Vice President, Product and Technology Marketing at MediaTek
CAMON 40 Series Powered by AI One-Tap FlashSnap Revolutionizes Smartphone Snapshot Photography
TECNO’s Global Product Launch Officer, Olivier Mas, officially unveiled TECNO’s next-generation AI-driven products. Attendees at TECNO’s launch event witnessed the highly anticipated debut of TECNO’s new CAMON 40 Series, a device that embodies TECNO’s legacy of excellence in mobile imaging. Featuring One-Tap FlashSnap Mode and TECNO AI, the series sets a new benchmark in smartphone photography, delivering exceptional snapshot capabilities and AI-enhanced user experiences.
Olivier Mas, TECNO Global Product Launch Officer
The CAMON 40 Series exemplifies a commitment to innovation that transcends hardware and software, extending into strategic partnerships that deliver cutting-edge AI solutions to emerging markets. Matt Waldbusser, Managing Director of Global Solutions and Consumer AI at Google Cloud, remarked, “Our collaboration with TECNO on the CAMON 40 Series is a standout example. Leveraging Google Cloud’s capabilities, we’ve introduced groundbreaking features such as Ask Ella, AI Image Generator, AI Writing, and AI Translate. I am particularly impressed by the industry-leading and competitive edge of some of these innovations. For instance, TECNO’s AI supports text translation in 136 languages, voice translation in 44 languages, and photo translation in 51 languages. We are excited to further strengthen our partnership with TECNO, unlocking limitless potential to bring advanced yet practical AI capabilities to emerging markets in a convenient and secure manner.”
Matt Waldbusser, Managing Director of Global Solutions and Consumer AI at Google Cloud
The CAMON 40 Series’ innovative One-Tap FlashSnap leverages AI to enhance imaging capabilities, revolutionizing mobile photography. AI optimizes camera startup and continuous shooting for instant captures, while AI-powered multi-frame processing intelligently reduces noise and enhances details, delivering sharper, more refined images. Additionally, the BestMoment algorithm analyzes motion patterns, automatically selecting the optimal frames for precise, high-quality shots in dynamic scenarios, ensuring users an unparalleled mobile imaging experience.
TECNO CAMON 40 Demonstrates the Cutting-Edge FlashSnap Capability
To delve deeper into the imaging prowess of the CAMON 40 Series, TECNO invited Frédéric Guichard, CEO of DXOMARK, to share the image performance of CAMON 40 Pro. Frédéric highlighted, “The CAMON 40 Pro 5G has demonstrated exceptional imaging and performance capabilities in our rigorous evaluations. We’ve been particularly impressed with photo performance being the best for devices under 600$, and the 1st eligible device to our Smart Choice Label.”
Onsite photo of Frédéric Guichard, CEO of DXOMARK
Beyond its advanced rapid-capture functionality, the integration of TECNO AI further enhances the device’s capabilities. Intelligent imaging, a 360° AI Call Assistant, and productivity tools elevate creativity and efficiency. Powered by MediaTek’s latest chipsets, the series ensures smooth performance, fast processing, and extended battery life. With a sleek, durable, and water-resistant design, it seamlessly blends style with practicality for modern users.
MEGABOOK S14, the World’s Lightest 14-inch OLED Laptop, Inspires Creators and Game Lovers
The MEGABOOK S14 is TECNO’s first OLED laptop and the industry’s lightest 14-inch OLED laptop, featuring a 2.8K OLED display and incredibly weighing only 899g (31.7oz). The laptop is equipped with the outstanding power of the Snapdragon® X Elite compute platform, the flagship chipset for AI PCs from Qualcomm Technologies, and integrates TECNO’s world’s first self-developed edge-side large-scale AI model, to achieve AI-enhanced multitasking.
World’s Lightest 14-inch Laptop MEGABOOK S14
Specifically designed for next-gen AI productivity, TECNO AI enhances the Ella AI Assistant, AI-powered PPT generation, AI-driven image search, smart albums, and offline meeting transcription with multilingual support. The External Graphics Dock, equipped with a powerful NVIDIA graphic card, delivers scalable, high-performance capabilities for design, gaming, and content creation. The laptop’s 2.8K OLED display with a 120Hz refresh rate ensures exceptional visuals, while DTS:X Ultra dual 2W speakers, Wi-Fi 6E, fingerprint login, and PC Manager optimize connectivity and user experience.
TECNO’s strategic partnership with Qualcomm Technologies was a highlight of the TECNO AI Ecosystem Product Launch event, demonstrating a shared vision for the future of AI PCs. Kedar Kondap, SVP & GM of Compute and Gaming at Qualcomm, took the stage to discuss the integration of Qualcomm’s cutting-edge PC chipset into the new MEGABOOK S14 laptop, underscoring TECNO’s commitment to delivering high-performance computing solutions.
Kedar Kondap, SVP & GM of Compute and Gaming at Qualcomm
In addition, TECNO also introduced several standout new products. The featherlight 999g (35.2oz) ultrabook MEGABOOK T14 Air, features high-speed storage and LPDDR5 memory, while the ultra-thin, all-metal MEGABOOK K15S, equipped with a powerful 70Wh battery and supported by a 65W PD GaN charger, offers a smarter and more long-lasting user experience. Both devices are empowered by TECNO AI with advanced AI capabilities such as AI Album and AI Voice Assistant, making them perfect companions for all aspects of life.
The Next Game-Changing Tech Innovation: See the World with the TECNO AI Glasses Series
TECNO’s new AI Glasses Series also took center stage with the introduction of TECNO AI Glasses Pro and TECNO AI Glasses, reimagining eyewear with cutting-edge imaging, intelligent interactions, and a sleek aesthetic. The TECNO AI Glasses feature an aviator design, while the Pro model showcases a browline style, both embodying timeless elegance and modern fashion.
TECNO AI Glasses Redefine the Way People See the Future
Equipped with a 50MP high-definition camera, the series integrates an OV50D sensor, a 100° ultra-wide-angle custom lens, and an AI ISP imaging chip, forming a mobile-grade imaging system. This system lets users capture stunning, high-resolution photos with advanced AI noise reduction and HDR capabilities. With real-time translation supporting over 100 languages, TECNO AI’s Ella empowers accurate translation even for less common languages, as well as voice control, AI-powered object recognition, and intelligent information summaries for ultimate convenience.
Additionally, the AI Glasses Pro features a MicroLED display with 7th-gen resin waveguide technology, offering a 30° field of view, over 1,500 nits of brightness AR display, and a lightweight, ultra-thin design. The AR display allows users to effortlessly enjoy features like translation display, navigation, information prompts, and teleprompting.
Equipped with a 250mAh battery, these glasses offer over 11 hours of music playback and 8 hours of mixed use with just 30 minutes of charging. An advanced ultra-linear speaker, bass enhancement, and spatial sound deliver an immersive audio experience, while Wi-Fi 6 and Bluetooth 5.4 ensure seamless connectivity.
With these innovative launches, TECNO is setting new standards in mobile imaging and AI-enhanced technology, shaping a more connected and empowered future for consumers in emerging markets. Once again, TECNO has showcased its cutting-edge innovation on the global stage at MWC. With the brand essence of “Stop at Nothing”, TECNO’s relentless pursuit of innovation is making AI-powered technology more accessible, allowing consumers to experience the future ahead of time.
Solomon Obwot is a tech writer based in Kampala, Uganda, with extensive experience in the local tech startup ecosystem. He covers the latest news and analysis on consumer tech, writes in-depth smartphone reviews, and conducts insightful interviews with industry experts. Solomon is also a passionate podcaster, sharing his knowledge and engaging in discussions about Africa’s rapidly growing tech landscape. Send emails to [email protected]
Type your email…